With more and more organizations and users adopting the Microsoft new Edge Chromium based browser. One of the most common requests are setting the default search provider. The most common request I get is setting it to Google but there are other providers out there and even specific ones for some systems and sites.
Finding the search provider string
First we need to find the search provider string that is supposed to be entered. The easiest way I’ve found, is actually using the browser to first visit the site and using the built in auto discover let Edge find the correct search terms and extracting them.
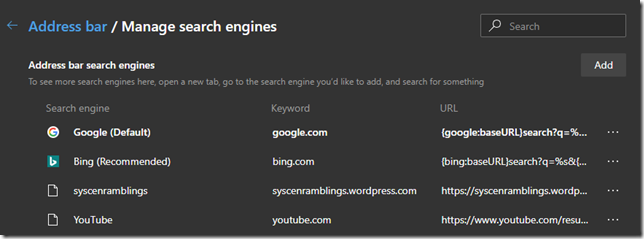
Let’s start by putting in “edge://settings/searchEngines” in the address field and you will end up on the correct page. In here all the search providers are already listed for you.
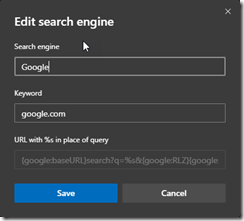
Hittig the … and then Edit, at the end will give you some options for that specific provider. You can set the name and the keyword. You will also have a locked field for URL. The URL part is what you need to use in a GPO or MDM later.
Setting the policies needed
Now all that remains is setting the policies needed. For this to work you will need to have the admx templates for Microsoft Edge. The templates can be found here Edge MSI and ADMX download
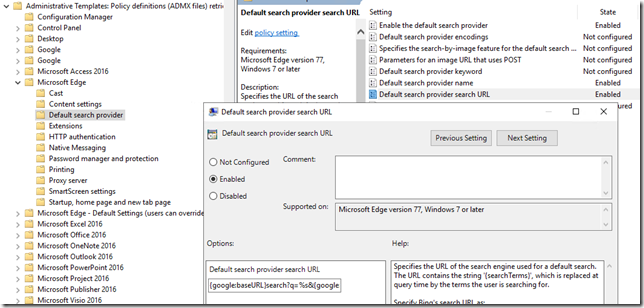
Next you need to edit the settings found under either User Configuration / Policies / Administrative Templates / Microsoft Edge / Default search provider or Computer Configuration / Policies / Administrative Templates / Microsoft Edge / Default search provider. Note that one location is enough as long as it linked to the correct type.
Configure the Default search provider URL and past the URL copied from the previous section.
Make sure to also configure Enable the default search provider. As an optional you can specify how the search provider name will be displayed by setting the Default search provider name. All settings are visible in the screenshot above.
Summary
This way you can configure any search provider you want, and even take it a step further and configure a predefined list using other GPO/MDM options. The new Edge policies really make this a enterprise class browser.
/Peter