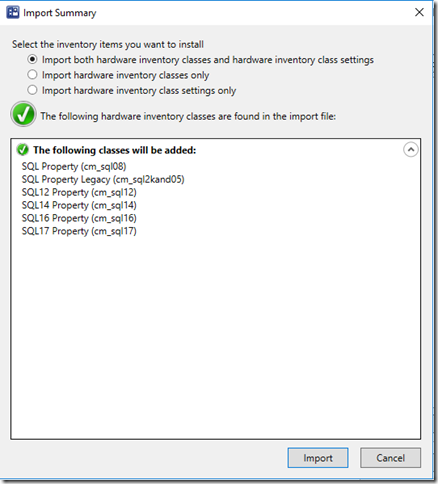
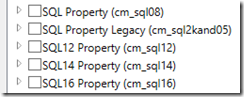
// SQL 2017 Properties
//———————————————
ServiceName,SqlServiceType from sqlServiceAdvancedProperty”},ViewSpaces{“\\\\.\\root\\microsoft\\sqlserver\\computermanagement14”}, dynamic,
Provider(“MS_VIEW_INSTANCE_PROVIDER”)]
[PropertySources{“IsReadOnly”} ] boolean IsReadOnly;
[PropertySources{“PropertyIndex”},key ] uint32 PropertyIndex;
[PropertySources{“PropertyName”},key ] string PropertyName;
[PropertySources{“PropertyNumValue”} ] uint32 PropertyNumValue;
[PropertySources{“PropertyStrValue”} ] string PropertyStrValue;
[PropertySources{“PropertyValueType”} ] uint32 PropertyValueType;
[PropertySources{“ServiceName”},key ] string ServiceName;
[PropertySources{“SqlServiceType”},key] uint32 SqlServiceType;
};
// SQL 2016 Properties
//———————————————
ServiceName,SqlServiceType from sqlServiceAdvancedProperty”},ViewSpaces{“\\\\.\\root\\microsoft\\sqlserver\\computermanagement13”}, dynamic,
Provider(“MS_VIEW_INSTANCE_PROVIDER”)]
[PropertySources{“IsReadOnly”} ] boolean IsReadOnly;
[PropertySources{“PropertyIndex”},key ] uint32 PropertyIndex;
[PropertySources{“PropertyName”},key ] string PropertyName;
[PropertySources{“PropertyNumValue”} ] uint32 PropertyNumValue;
[PropertySources{“PropertyStrValue”} ] string PropertyStrValue;
[PropertySources{“PropertyValueType”} ] uint32 PropertyValueType;
[PropertySources{“ServiceName”},key ] string ServiceName;
[PropertySources{“SqlServiceType”},key] uint32 SqlServiceType;
};
// SQL 2014 Properties
//———————————————
ServiceName,SqlServiceType from sqlServiceAdvancedProperty”},ViewSpaces{“\\\\.\\root\\microsoft\\sqlserver\\computermanagement12”}, dynamic,
Provider(“MS_VIEW_INSTANCE_PROVIDER”)]
[PropertySources{“IsReadOnly”} ] boolean IsReadOnly;
[PropertySources{“PropertyIndex”},key ] uint32 PropertyIndex;
[PropertySources{“PropertyName”},key ] string PropertyName;
[PropertySources{“PropertyNumValue”} ] uint32 PropertyNumValue;
[PropertySources{“PropertyStrValue”} ] string PropertyStrValue;
[PropertySources{“PropertyValueType”} ] uint32 PropertyValueType;
[PropertySources{“ServiceName”},key ] string ServiceName;
[PropertySources{“SqlServiceType”},key] uint32 SqlServiceType;
};
// SQL 2012 Properties
//———————————————
ServiceName,SqlServiceType from sqlServiceAdvancedProperty”},ViewSpaces{“\\\\.\\root\\microsoft\\sqlserver\\computermanagement11”}, dynamic,
Provider(“MS_VIEW_INSTANCE_PROVIDER”)]
[PropertySources{“IsReadOnly”} ] boolean IsReadOnly;
[PropertySources{“PropertyIndex”},key ] uint32 PropertyIndex;
[PropertySources{“PropertyName”},key ] string PropertyName;
[PropertySources{“PropertyNumValue”} ] uint32 PropertyNumValue;
[PropertySources{“PropertyStrValue”} ] string PropertyStrValue;
[PropertySources{“PropertyValueType”} ] uint32 PropertyValueType;
[PropertySources{“ServiceName”},key ] string ServiceName;
[PropertySources{“SqlServiceType”},key] uint32 SqlServiceType;
};
// SQL 2008 Properties
//———————————————
ServiceName,SqlServiceType from sqlServiceAdvancedProperty”},ViewSpaces{“\\\\.\\root\\microsoft\\sqlserver\\computermanagement10”}, dynamic,
Provider(“MS_VIEW_INSTANCE_PROVIDER”)]
[PropertySources{“IsReadOnly”} ] boolean IsReadOnly;
[PropertySources{“PropertyIndex”},key ] uint32 PropertyIndex;
[PropertySources{“PropertyName”},key ] string PropertyName;
[PropertySources{“PropertyNumValue”} ] uint32 PropertyNumValue;
[PropertySources{“PropertyStrValue”} ] string PropertyStrValue;
[PropertySources{“PropertyValueType”} ] uint32 PropertyValueType;
[PropertySources{“ServiceName”},key ] string ServiceName;
[PropertySources{“SqlServiceType”},key] uint32 SqlServiceType;
};
// SQL 2000/2005 Properties
//———————————————
ServiceName,SqlServiceType from sqlServiceAdvancedProperty”},ViewSpaces{“\\\\.\\root\\microsoft\\sqlserver\\computermanagement”}, dynamic,Provider(“MS_VIEW_INSTANCE_PROVIDER”)]
[PropertySources{“IsReadOnly”} ] boolean IsReadOnly;
[PropertySources{“PropertyIndex”},key ] uint32 PropertyIndex;
[PropertySources{“PropertyName”},key ] string PropertyName;
[PropertySources{“PropertyNumValue”} ] uint32 PropertyNumValue;
[PropertySources{“PropertyStrValue”} ] string PropertyStrValue;
[PropertySources{“PropertyValueType”} ] uint32 PropertyValueType;
[PropertySources{“ServiceName”},key ] string ServiceName;
[PropertySources{“SqlServiceType”},key] uint32 SqlServiceType;
}; |